Most people got administrator account password blank, easy way to get onto their shares. Download Patches from Microsoft. When you infect a host or find a infected host, it's time to connect. Apply the patch as soon as possible, regardless. What is a IP address?
| Uploader: | Fenrizuru |
| Date Added: | 7 April 2016 |
| File Size: | 26.76 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 20249 |
| Price: | Free* [*Free Regsitration Required] |
IP's that does not really exist, or it does excist but it is someone else's Exploi, not yours. This will show you their MAC address as well as their currently logged on user. Download Patches from Microsoft. Without UrlScaninstead of the expected: The Microsoft patches are the only ways to completely fix this vulnerability.
Download Supercan and put in a IP range. Use share drive, run cmd C: If the patch for this issue is installed on a system with one of these versions of ntoskrnl. Administrator account is needed. Remember the routers IP sxploit could differ from the example above.
Its a software or hardware device which can block or permit certain ports or IP's or certain kinds of data.
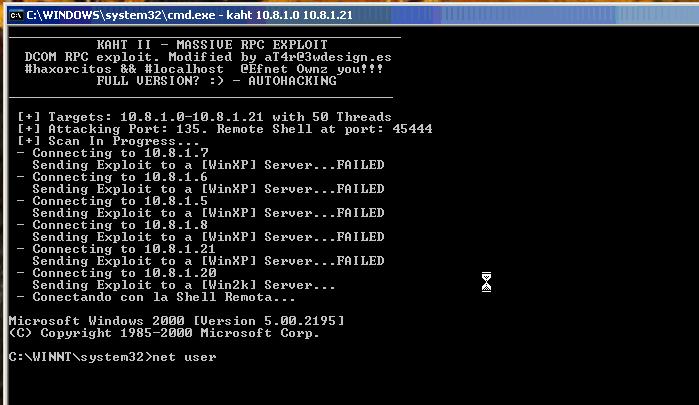
Full Disclosure: KaHT II - Massive RPC Dcom exploit..
Then choose who u want to send to and from who u want kaut email to be from. Always remember to rename the file, change the program icon and the put a password on the server file. Make sure you use URLScan version 2. Performing initial Telnet brute force using Hydra cat pass.
Download NetBiosBomber, choose the target and choose which OS and you ready to makes someone's life hell. IIS - Internet information server. He has made explot the binary and the source code available: The webcast is archived and is highly recommended if you want to learn more about this vulnerability.
His analysis demonstrates how the exploit works, and provides screenshots of the exploit being performed in a lab environment.
Proof of concept exploit codes and vulnerabilities
What is IP ping? Check this page for new exploits: Example shows hydra in use to brute-force the Cisco IOS Telnet service password, using a list of default Cisco passwords from pass. Every program running on your PC which has some network function uses a specific port to send an receive data though.
If they are running a firewall, they will see where all this traffic is coming from and they will see it's YOU.
Their username can also be useful if you would like to know this persons name. Their PC name can be their own name or company name.
Hacking D Worldd | Hackers Heaven
By analyzing the results, I find kzht the server isn't susceptible to these issues. Another way is to telnet to the IP on port Monitor information sources for additional alerts regarding possible attack eploit.
Group to admin C: This exploit bruteforces the return address to get into the system. All of this can only be retrieved if the person has a network card installed on their PC. There is a few IIS tutorials in Windows hacker misc section.

Each trojan uses a diffident port.


Комментариев нет:
Отправить комментарий